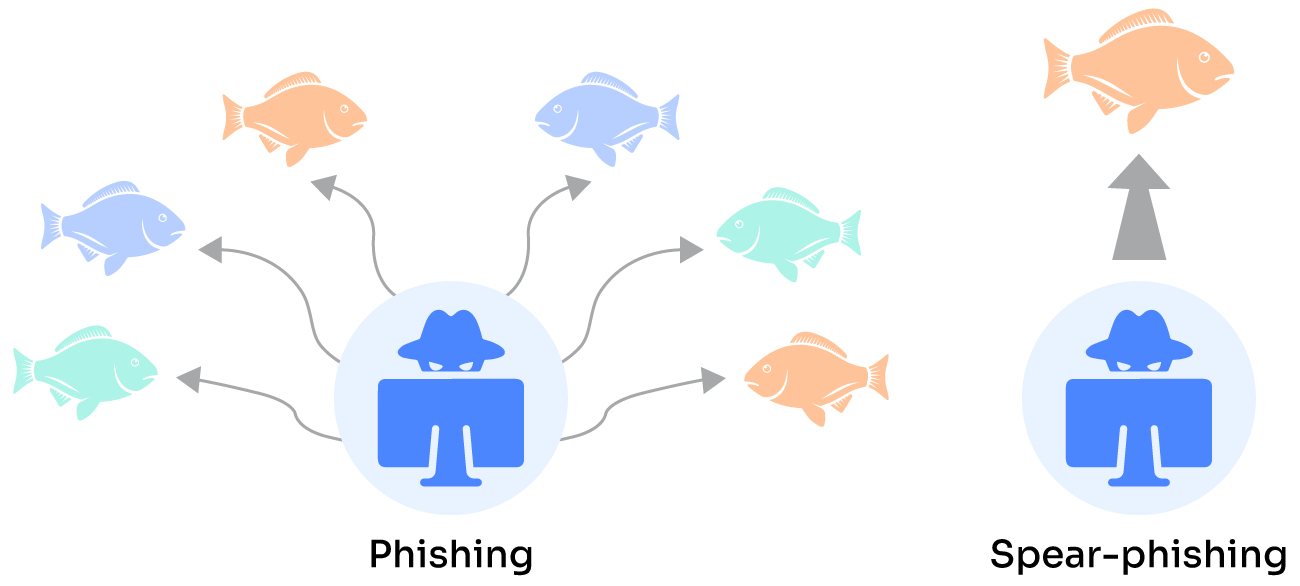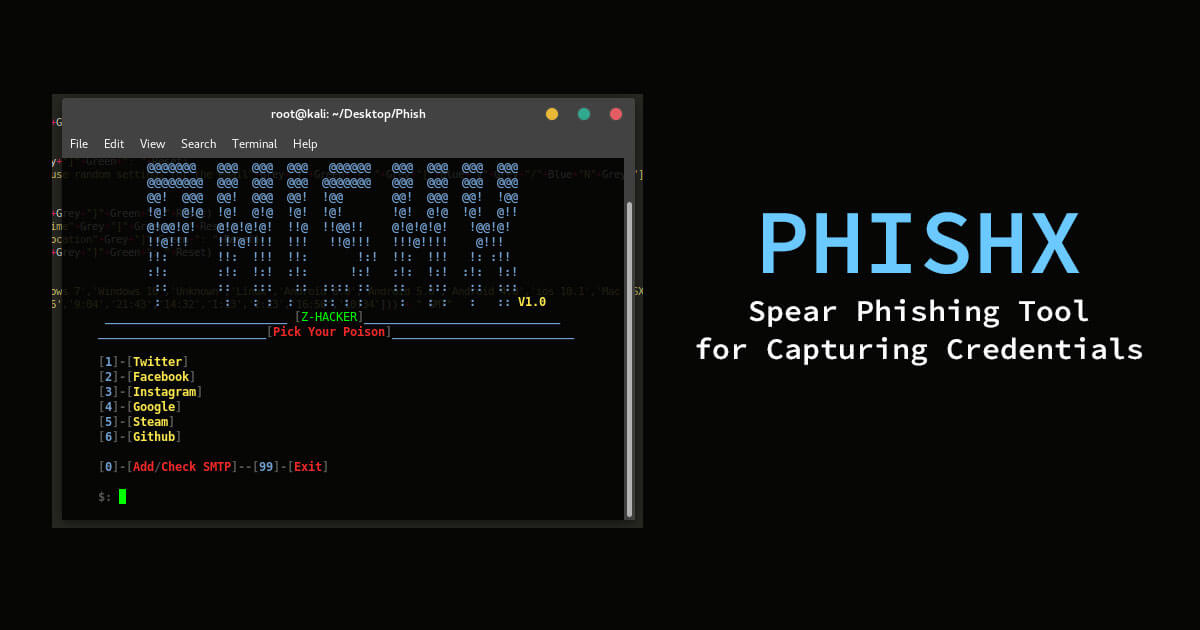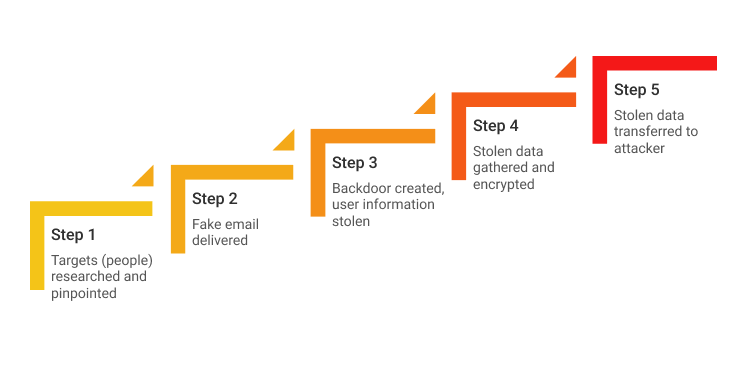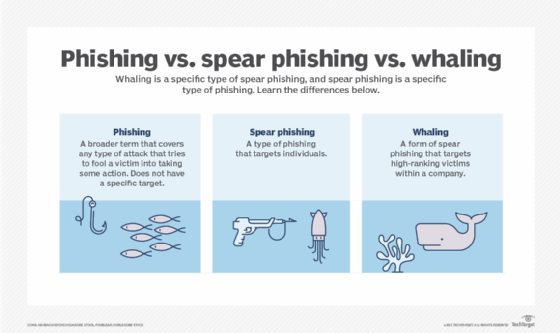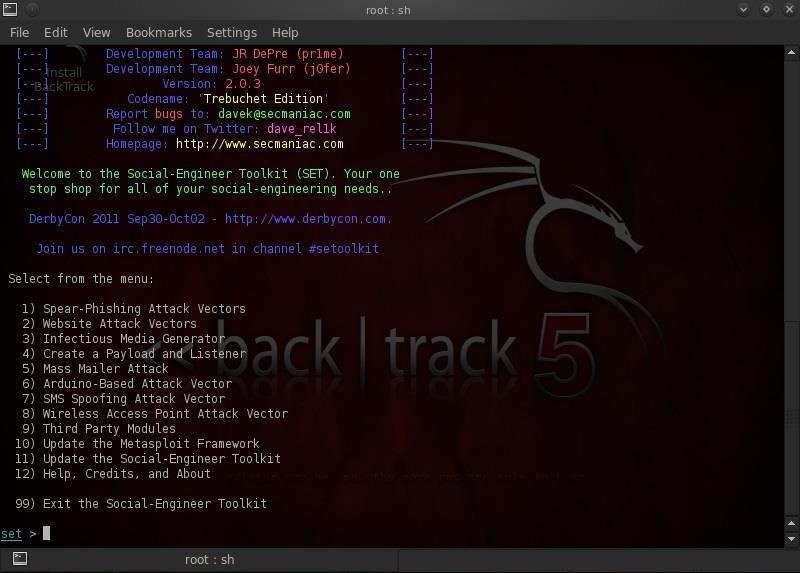
Hack Like a Pro: How to Spear Phish with the Social Engineering Toolkit (SET) in BackTrack « Null Byte :: WonderHowTo

AI Spear Phishing Tool Sales Boom on the Dark Web | 2024 Cybersecurity Predictions | During 2024, we expect to see at least one AI/ML-based tool to help automated spear phishing show
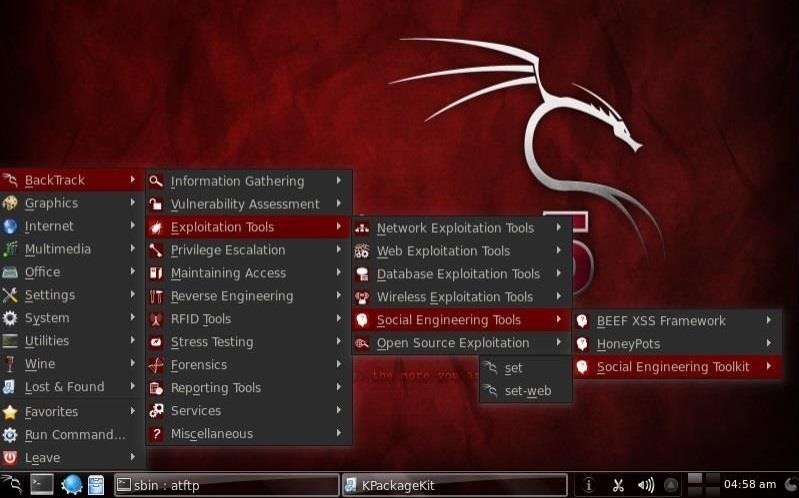
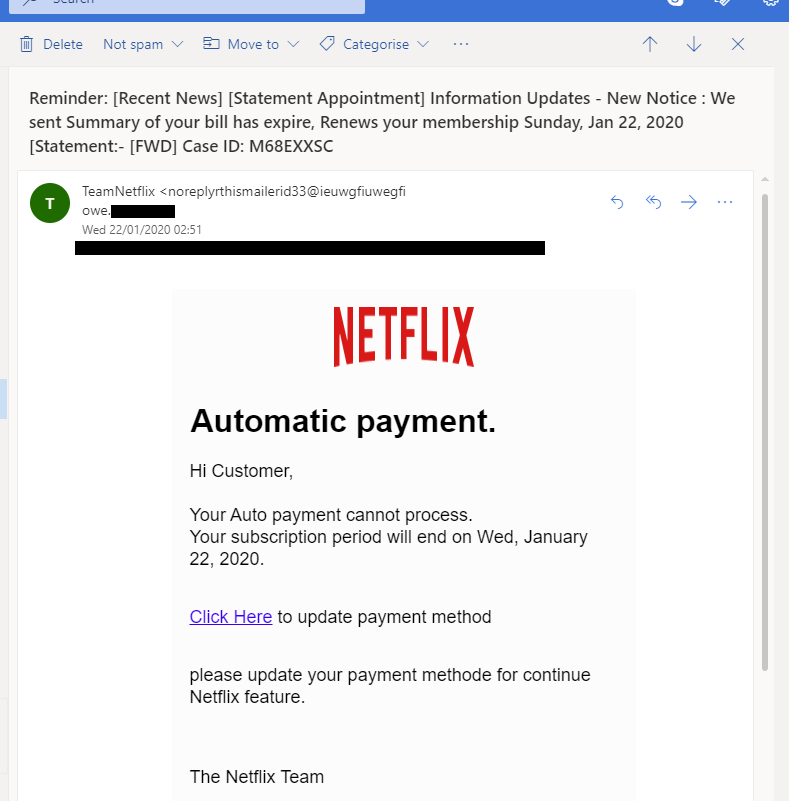

![Top 8 Different Phishing Tools with Features [2023] Top 8 Different Phishing Tools with Features [2023]](https://cdn.educba.com/academy/wp-content/uploads/2021/07/Phishing-Tools.jpg)